Table of Contents
Welcome to Identity.com, a revolutionary platform that is reshaping the global perception of identity through cutting-edge blockchain technology.
In the digital age, identity verification has become an integral part of our everyday lives. As we navigate through various online platforms, the need for a secure and efficient identity verification process has never been more critical.
The New Identity Economy
Identity.com is more than just a platform; it’s an innovative ecosystem that is reshaping the concept of identity verification. We call this transformative shift the New Identity Economy. This platform connects those who need to confirm an identity with those who need their identity validated. The marketplace aims to enhance the identity verification process for all participants by:
- Giving individuals more control and security over their personal data.
- Lowering the risks associated with managing and storing personal information.
- Creating a steady revenue stream for entities that validate identities.
- Emphasizing the importance of identity verification over the exchange of personal data.
We see Identity.com playing a significant role in the future of identity. However, decentralized identity extends beyond a single identity ecosystem. Revolutionizing how we authenticate our identities requires a global collaborative effort. To help more people understand the importance of our work, we’ve created a beginner’s guide that simplifies Identity.com in non-technical terms.
Participants of the Identity.com Ecosystem
The Identity.com ecosystem comprises three distinct types of participants: Identity Validators, Identity Requesters, and Users through ‘Credential Wallets’.
Identity Validators
Validators are the backbone of the Identity.com ecosystem. They are entities capable of verifying information related to a user’s identity. The validators on Identity.com are likely similar to those you currently use, including banks, mobile phone providers, specialized identity verification companies, and government agencies.
Identity Requesters
Requesters are the ecosystem’s customers. They are entities that need to verify information related to a user’s identity before granting access to a product or service. A requester could be a nightclub bouncer verifying someone’s age, a leasing agent conducting a background check before renting, or a border agent checking travel credentials.
Users through ‘Credential Wallets’
Users are the beneficiaries of the Identity.com ecosystem. All interactions and transactions are initiated by the user. They have access to a secure mobile app that acts as their Credential Wallet, like the Civic App or other apps that implement the associated Identity.com toolkit.
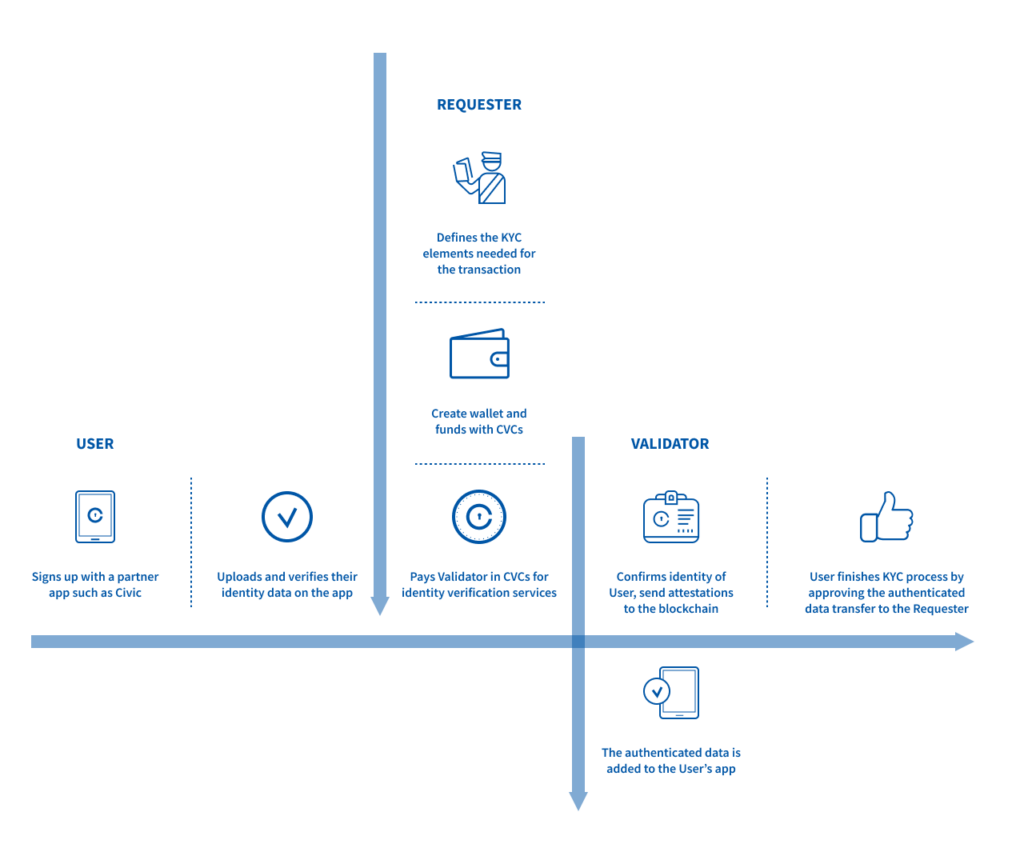
Identity.com Verification Process Diagram
The Identity.com Verification Process
All Identity.com interactions are initiated by a user. Suppose a user wants to apply for a service or register with a vendor. For instance, logging into a gambling website with the Civic App. Because gambling is age-restricted, a user must prove they are 21 years of age or older to access the website. In this case, the requester is the gambling website.
When a user visits the gambling website, the site prompts them to verify that they are over 21 years of age. Instead of entering a birthdate or registering with the website, the user simply scans a QR code on the requester’s website with the Civic App. This QR code informs the user’s app about the type of verified credentials required by the requester and the validators that the requester will accept verified credentials from.
A verified credential is a piece of information, like an address, a birthdate, or a social security number, validated by a validator.
If the user already has the verified credential stored on their mobile device, they can share it with a requester immediately. If not, the user will need to get their credentials validated by an approved validator, which usually takes a few minutes. Once the user has the required verified credentials, they can share them with the requester.
When a user shares a verified credential with a requester, the validator is paid by the requester for their validation in CVC tokens. Users never pay for identity verification. Furthermore, escrow accounts facilitate the payment process for requesters and validators. Smart contracts also play a crucial role in eliminating the need for direct interaction between them. This is why CVC tokens are vital to the marketplace economy. For a non-technical explanation, you can read more in our Token Behavior Model White Paper.
Benefits of Reusable Verifiable Credentials
Once this interaction is completed, all the verified credentials remain on a user’s mobile device, and these verified credentials can be reused. This reusability simplifies and streamlines the identity verification process. If multiple requesters need the same verified credentials, there is no need to undergo multiple rounds of identity verification.
We use the Civic App as an example because, currently, Civic is the only company operating in the Identity.com marketplace. However, in the future, the Civic App could be any company that decides to develop on the Identity.com marketplace.
Decentralized and Open-Sourced
Identity.com is decentralized by design. This means that anyone can leverage Identity.com without the need to go through a central authority or managed service. In the identity verification marketplace, all ecosystem participants actively control the sharing of information and their engagement with others. Most importantly, the decentralized design enables the storage of user information locally on a mobile device.
Applications of game theory and smart contracts, rather than a central body, will govern Identity.com. So, how does this work? Automated processes will be in place, providing incentives for good behavior and imposing penalties for bad behavior. If behaving badly carries a higher cost than behaving well, all rational actors should strive to abide by the rules in the platform. This will result in a trustworthy and growing ecosystem.
Identity.com is also open source by design. This belief stems from the idea that no single company should own identity. Interacting with a decentralized blockchain can be challenging, and open-sourcing these layers, like libraries, toolkits, and smart contracts, makes it easier for other organizations to leverage Identity.com.
Any organizations that want to develop on top of Identity.com and leverage the identity verification infrastructure are welcome to build or connect their own identity solutions.
The Vision of Identity.com
At Identity.com, we envision a world where everyone has a digital identity that they control. Achieving this goal requires a complete transformation in our perception of identity, and it requires a community that shares these values. That is why we created the Identity.com platform.

